Enterprises take access control seriously. No one can enter the premises without permission and authentication. Every individual needs to use an access card or a similar mechanism to enter or exit the premises, so security personnel can track who comes in and out at what times.
This concept of security, involving guards, biometric systems, and access control cards, prevents intruders from entering, accessing restricted areas, and obtaining information critical to your business.
In the digital era, all sensitive data and business operations occur within a digital network, involving both cloud and on-premises hardware and systems. So, applying the same security rules for access control to this digital infrastructure is indispensable. However, many organizations do not implement proper admission control, thereby putting enterprise security at risk. This is where network admission control (NAC) comes in.
NAC serves the same purpose as physical access control: denying unauthorized personnel access and ensuring only authorized, compliant, and trusted entities can connect to your network.
This article explains network admission control, its importance, how it works, and how to implement NAC in an enterprise setup
What is Network Admission Control?
Network admission control (NAC) is a cybersecurity framework that controls access of devices and users to an enterprise network. NAC aims to manage who can access what resources and under what conditions.
That way, it is quite akin to physical access control; NAC extends those principles into the digital ecosystem. While access control uses doors, keycards, guards, and locks, NAC controls access to the enterprise digital ecosystem by combining identity, authentication, and policy enforcement using a logical framework built on:
- Identity and Access Management (IAM)
- Role-Based Access Control (RBAC)
- User authentication mechanisms
However, NAC is more advanced than traditional access control in certain ways. For instance, depending on your predefined credentials, access control allows or restricts access after the security personnel verify your ID and confirm who you are. If you get access, it means you are considered a trusted person until you leave the premises.
In contrast, enterprise Network Admission Control (NAC) operates dynamically. It goes beyond verifying your ID and confirming who you are; it also verifies other vital details, such as what you are bringing in and your security compliance. NAC ensures that only trusted, healthy, and compliant devices connect to your network.
In practice, NAC:
- Authenticates devices
- Assesses their compliance
- Implements network admission control policy enforcement rules in real time
- Grants or restricts network access dynamically based on compliance status
What Happens If You Have A Network Without Admission Control?
Failing to implement Network Admission Control solutions leaves your network open for attack. Without NAC to verify devices and their security compliance, any device, including rogue, unmanaged, or unauthorized ones, can connect to your network freely. If attackers manage to connect to your network, they can introduce malware, data exfiltration tools, or vulnerabilities, infecting your systems and stealing your data.
A lack of Network Admission Control can be disastrous for an enterprise network that supports remote work, IoT devices, and a BYOD (Bring Your Own Device) culture. Such a network faces an expanded threat surface, as these devices can serve as entry points for cyberattacks, especially if they have a weak security posture. An NAC significantly reduces unauthorized entry points and the risk of unauthorized or non-compliant devices entering the network.
Further, without enterprise network admission control solutions, IT teams cannot have the visibility needed to monitor who accesses critical systems.
Since these risks are best mitigated proactively before they can occur, it is indispensable to have a robust network admission control implementation strategy.
Modern Access Control Frameworks for NAC
There was a time when organizations predominantly relied on on-prem infrastructure, including devices, software systems, and storage. But that model no longer works in the era of mobile devices, SaaS, and cloud-based systems and storage. A cloud-first approach is inevitable. However, this approach brings in the complexities of distributed teams and device diversity.
Traditional security boundaries that secured the enterprise networks in the past lack clear demarcation. The recent paradigm shift necessitates frameworks that integrate network admission control into broader architectures like Zero Trust and identity-based security.
Modern frameworks enable:
- Zero Trust Network Access (ZTNA), which treats every connection, both internal and external, as untrusted, even if it was previously authenticated. It forces you to verify, authenticate, and authorize every connection continuously to ensure network integrity.
- Identity-Based Security that grants access only after verifying the digital identities of users/devices, rather than focusing on their network location. It promotes consistent, context-aware security across hybrid and cloud environments.
- Continuous Authentication that works in real time throughout the session, constantly evaluating behavior, device health, and contextual signals to authenticate users, or adjust/revoke their access, instead of providing access through a one-time login. This approach ensures sustained compliance.
- Role-Based Access Control (RBAC), which dynamically assigns access privileges to each connection based on organizational roles and responsibilities, enabling granular, least-privileged access that aligns with job functions.
NAC is at the core of this ecosystem, working as a foundational component and a gatekeeper that enforces these frameworks at the network layer. It forces all devices, both human-operated (such as a workstation) and autonomous (such as an IoT device), to adhere to policy; only then does it deem the device trusted.
From Policy to Practice: Network Admission Control Implementation
The success of an organization’s network admission control implementation and cybersecurity strategy depends on:
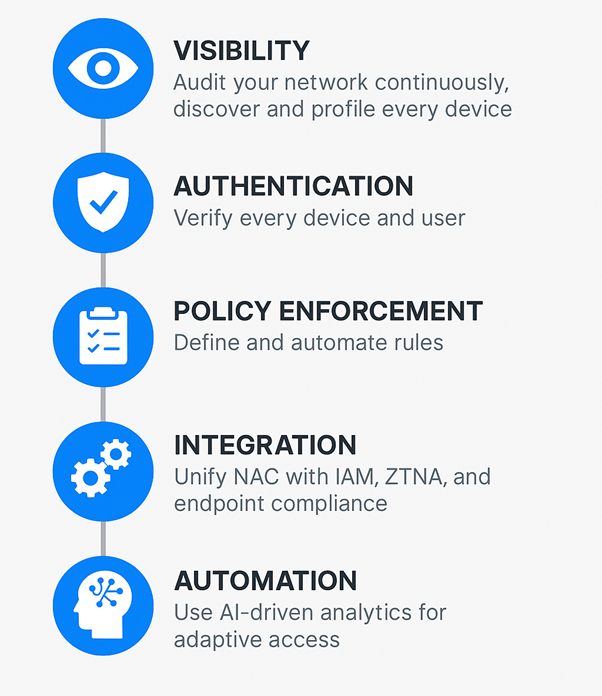
- Visibility: Audit your network continuously, discover every connected device — including IoT and guest systems — and profile them. Make sure that every device is accounted for.
- Authentication: Verify the legitimacy of every device and user. Implement a verification method, be it certificate-based or identity-based, for that purpose.
- Policy Enforcement: Define a set of rules and automate their implementation to ensure endpoint compliance and access privileges.
- Integration: Create a unified network security system, integrating NAC with IAM, ZTNA, and endpoint compliance.
- Automation: Leverage AI-driven analytics to identify anomalies, isolate risky endpoints, and adapt access dynamically.
Network Admission Control for IoT can be complicated. Multiple types of IoT devices may connect to an enterprise network. Each of these devices may feed data into a different system in the network, requiring different levels of access. So, they may need different permissions, in addition to the automation required to authenticate these unmanned devices.
Device profiling and segmentation are indispensable for this. You must categorize these devices by type — such as sensors or industrial controllers — and tailor access policies that balance functionality with security.
When you automate network admission control policy enforcement and integrate it into broader cybersecurity strategies, NAC evolves from a gatekeeper into an intelligence-driven access orchestrator.
Final Thoughts: The New Definition of “Access”
An office that allows unrestricted access to anyone would be unthinkable. It should be the same for your enterprise network. Yet many enterprises still run “open-door” networks. It is evident that securing the digital network with network admission control is as important as securing your premises with access control; they are foundational.
By integrating NAC with various cybersecurity tools and aligning it with Zero Trust, identity-based security, and continuous authentication, you can ensure that no user, device, or connection gets access automatically; they earn it every time.
In a business environment, where keeping your business safe and your business-critical information and data secure requires protecting both physical and digital assets, securing one without the other is incomplete. Admission control is no longer a network feature; it’s an organizational mindset.
FAQs
1. What is the purpose of network admission control?
Network admission control aims to ensure only authorized and compliant devices connect to enterprise networks. It protects data integrity, enforces security policies, and maintains endpoint compliance.
2. What is admission control in networking?
Admission control in networking is the process of regulating device and user entry into a network. It controls user entry using authentication, compliance, and policy enforcement. It enables trusted access and prevents unauthorized or risky connections.
3. What is NAC used for?
NAC is used to identify, authenticate, and assess devices before granting network access. It enforces enterprise security policies, supports Zero Trust principles, and enhances overall network visibility and control.
4. When should NAC be used?
NAC should be used whenever organizations need to secure hybrid, IoT, or BYOD environments, enforce endpoint compliance, implement Zero Trust strategies, and prevent unauthorized network access.
Here’s How You Can Engage with Us:
- Stay Connected: Follow our latest updates, insights, and events on LinkedIn.
- Collaborate with Us: Partner with us to enhance your IT infrastructure or cybersecurity systems.
Let’s work together to drive success and secure your enterprise.
Contact Us | Explore Our Services


