Enterprises are rapidly adopting cloud and hybrid environments, moving away from purely on-premises systems.
While endpoint security in hybrid environments is a concern, securing cloud-native applications is a major challenge in its own right. With widespread cloud adoption, enterprises operate across multiple cloud providers. They rely heavily on Kubernetes and deploy applications through automated CI/CD pipelines. These factors bring new challenges. Cloud adoption has brought flexibility, scalability, speed, and agility; at the same time, it has created hidden security gaps.
Traditional security systems have not kept pace with cloud adoption, mainly because they were not designed for the cloud; they were designed for static workloads, simpler identities, and less frequent application deployments. These tools are fragmented and work in silos. So, they do not offer complete visibility and context for the risks essential to securing the cloud. They do not offer proactive, end-to-end cloud security. There is a need to create dedicated security systems to holistically secure the cloud. This is where Cloud-Native Application Protection Platforms (CNAPP) come in.
This article explains how fragmented tools in dynamic cloud-native environments leave hidden gaps in cloud security. It introduces CNAPP as a unified platform that secures applications throughout the lifecycle and explains why it is essential for DevSecOps, Kubernetes security, and closing critical cloud security blind spots.
What Is CNAPP?
CNAPP (Cloud-Native Application Protection Platform) is a unified, overarching cloud security platform and architectural approach that integrates and consolidates multiple cloud security tools. It provides comprehensive, end-to-end protection for cloud-native applications throughout their entire lifecycle, from development to production.
In contrast to point solutions designed to protect a single layer, CNAPP unifies multiple cloud security capabilities into a single integrated platform, enabling you to gain complete visibility, prioritize risks, and ensure protection across infrastructure, workloads, identities, containers, and Kubernetes environments.
Empowering you to see all the hidden vulnerabilities with context, it lets you prioritize and address them before someone exploits them. By doing so, CNAPP security platform shifts cloud security from reactive defence to proactive risk management.
Why Traditional Cloud Security Approaches Fall Short
Traditional security approaches treat every aspect of the cloud as separate and use dedicated single-purpose point solutions for each: CSPM for misconfigurations, CWPP for workloads, CIEM for identities, and separate solutions for containers and Kubernetes. However, these tools operate in silos and do not offer comprehensive protection. Challenges in traditional cloud security include:
- Limited visibility: Traditional systems operate in silos and show only those risks within their scope of protection in isolation.
- Alert fatigue: These tools do not provide the context for risks. As a result, they alert you to everything they consider a risk, sending hundreds of false alarms that cause fatigue. Without context, security experts cannot see the seriousness of vulnerabilities. So, they cannot prioritize and fix the most important issues first. As a result, serious hidden risks can slip through your scrutiny.
- Reactive security: Traditional tools can detect issues only after deployment. So, they are reactive by design. Identifying risks early and fixing them prevents attackers from finding vulnerabilities and exploiting them. Cloud security requires a proactive approach.
- Limited DevSecOps alignment: Traditional solutions are not integrated into development workflows. So, the security checks happen late in the release cycle. Manual reviews and security findings before release push teams to the limit. It results in friction between security and development teams. Persistent last-minute fixes, delayed releases, and increased rework for developers slow down delivery and weaken overall cloud security posture.
As cloud environments scale, these gaps widen, and you are exposed to risks despite significant security investments.
CNAPP Benefits: Why Use CNAPP in Cloud-Native Environments?
Cloud-native environments are dynamic by nature, as resources spin up and down automatically, identities change constantly, and deployments happen multiple times a day. They need complete visibility into vulnerabilities and a proactive approach to fixing issues before they impact your business.
With CNAPP, you can:
- Reduce the attack surface.
- Detect, prioritize, and remediate critical risks faster.
- Improve compliance and governance.
- Streamline operations by consolidating tools and bringing all essential cloud security capabilities into a single platform.
- Align security with business agility and scaling needs.
CSPM vs CNAPP: Understanding the Difference
Cloud Security Posture Management (CSPM) identifies misconfigurations and compliance issues in cloud infrastructure. However, it does not protect runtime workloads, correlate identity risks, provide contextual risk prioritization, offer native Kubernetes security, or cover the full application lifecycle. It represents only one piece of the security puzzle.
In contrast, CNAPP goes beyond that. CNAPP adds runtime workload protection. It correlates identity, configuration, and workload risks, extends security into CI/CD pipelines, and provides context-aware risk prioritization.
In short, CSPM identifies and provides visibility into misconfigurations, while CNAPP, in addition to all that, provides context on risks, offering insights into which vulnerabilities matter most and need to be fixed first.
Core CNAPP Components
A Cloud-Native Application Protection Platform typically includes:
- Cloud Security Posture Management (CSPM), which continuously monitors cloud configurations to identify misconfigurations, compliance violations, and risky settings.
- Cloud Workload Protection Platform (CWPP) – a platform that protects workloads from runtime threats and exploits, safeguarding virtual machines, containers, and serverless functions.
- Cloud Infrastructure Entitlement Management (CIEM) that detects excessive permissions, privilege escalation risks, and identity-related attack paths across cloud services.
- Kubernetes and Container Security, which secures clusters, images, runtime behavior, and frequently-targeted orchestration layers from attackers.
- Infrastructure as Code (IaC) Security that scans templates and configurations before deployment and proactivelyidentifies security issues.
How does a CNAPP Close Security Gaps?
CNAPP platforms reduce complexity and improve security outcomes by ensuring:
- Unified visibility across the cloud, from cloud accounts and workloads to identities.
- Contextual risk prioritization based on exploitability and the impact of those risks on your business.
- Continuous monitoring from build-time to runtime.
- Native Kubernetes security without requiring multiple standalone add-on tools.
- DevSecOps-friendly integrations that fit into CI/CD workflows, providing actionable feedback and allowing developers to fix issues early.
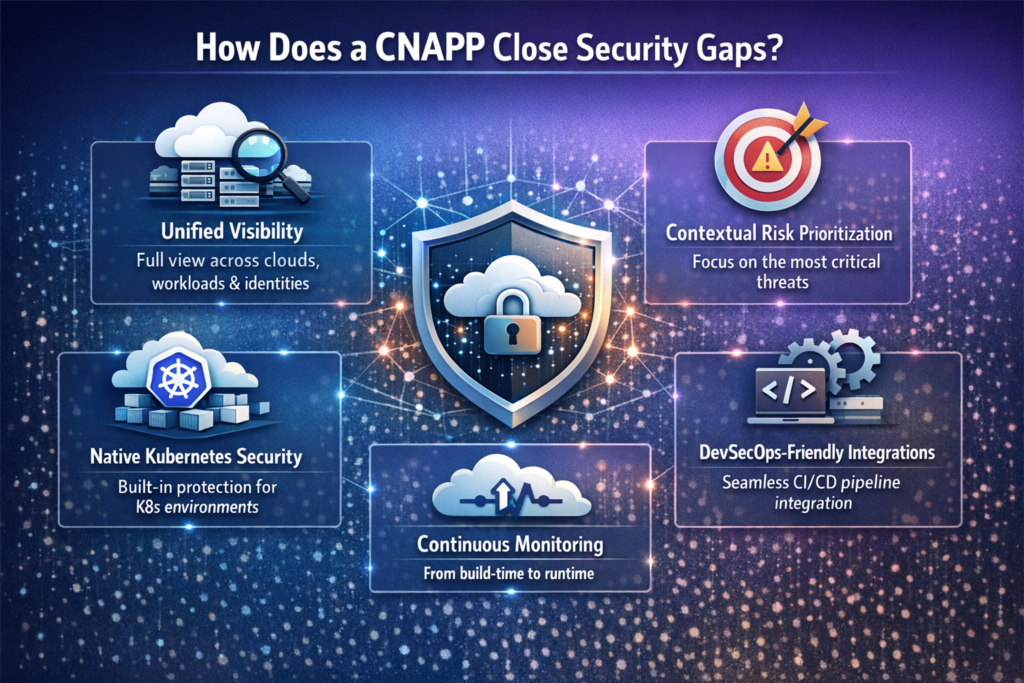
With these features, you can identify the most critical risks, prioritize and proactively fix them, rather than chasing false alerts and missing hidden vulnerabilities.
CNAPP for DevSecOps: Securing the Full Application Lifecycle
Detecting issues before release slows your teams down, forcing them to address the issues at the last minute. It causes consistent delays and slows down innovation. So, security can no longer be an afterthought. CNAPP offers numerous benefits and supports DevSecOps by embedding security throughout the application lifecycle, enabling issues to be detected and fixed proactively.
Shift-left security enables early detection of vulnerabilities, including misconfigurations, vulnerable dependencies, and insecure permissions, before applications are deployed to production. It achieves that by embedding security checks into design, coding, and CI/CD stages, making fixes faster, cheaper, and less disruptive to development velocity.
Seamless CI/CD pipeline integration enables CNAPP to scan infrastructure-as-code, container images, and configurations during build and deployment stages. So, developers get actionable feedback early and fix issues before production. In the meantime, security teams can maintain governance without blocking release velocity.
CNAPP provides actionable insights with context-based risk prioritization, rather than overwhelming you with hundreds of alerts that don’t matter most of the time. It correlates configuration issues, identity permissions, exposure, and runtime behavior to prioritize the most exploitable risks with the greatest potential to impact the business.
CNAPP enforces automated policies that scale with development velocity. So, security controls are applied consistently through automation, eliminating the need for manual reviews. Policies are embedded into CI/CD pipelines and cloud environments. As a result, security guardrails adapt automatically as applications, workloads, and deployments increase, so development does not slow down.
CNAPP Solutions for Kubernetes Security
Kubernetes is an integral part of the cloud-native architecture. However, they introduce new attack vectors that need to be addressed. So, CNAPP is foundational for running containerized workloads at scale. CNAPP addresses Kubernetes-specific risks by:
- Providing comprehensive security across clusters, nodes, and workloads.
- Monitoring runtime behavior for anomalies.
- Identifying misconfigurations and exposed services.
- Correlating Kubernetes risks with identity and network context.
CNAPP Implementation: Where to Start
Successful CNAPP implementation leads to comprehensive visibility, faster response, and a stronger cloud security posture. You can implement CNAPP by following these steps.
- Assess existing cloud security gaps and audit the tools you already have to identify tool overlap.
- Map the risks across configuration, identity, and workloads.
- Integrate CNAPP with cloud providers and CI/CD pipelines.
- Create alignment amongst SecOps, DevOps, and DevSecOps teams.
- Measure risk reduction and security maturity continuously.
Final Thoughts: Closing the Gaps That Matter Most
Cloud security gaps are often hidden, becoming visible only when bad actors exploit them. It is indispensable to have complete visibility of these gaps and ensure proactive security in the cloud. You cannot achieve that with fragmented traditional tools, limited context, and reactive controls.
CNAPP addresses these issues in increasingly complex cloud environments. It represents a strategic shift from fragmented security systems, bringing visibility, prioritization, and protection together under one unified platform. For enterprises that need to secure cloud-native applications, a CNAPP is indispensable.
FAQs
1. What is a CNAPP?
CNAPP is a unified cloud security platform that protects applications across build, deploy, and runtime by combining posture management, workload protection, identity security, and Kubernetes security into one framework.
2. What is the difference between CNAPP and CASB?
CNAPP secures cloud-native applications and workloads across their lifecycle. On the other hand, CASB focuses on monitoring and controlling user access, data security, and policy enforcement for SaaS applications used by enterprises globally.
3. What are the four types of cloud services?
The four cloud service models are Infrastructure as a Service, Platform as a Service, Software as a Service, and Function as a Service.
4. What are the four pillars of CASB?
The four pillars of CASB are visibility, data security, threat protection, and compliance. They enable you to consistently and securely monitor cloud usage, prevent data loss, detect threats, and meet regulatory requirements.


