A Modern, Risk-Based Approach
In today’s digital landscape, vulnerabilities are constantly identified, and threats can come from anywhere. The sheer number of vulnerabilities and the volume of security alerts organizations receive daily can be overwhelming.
But they cannot respond to all those alerts and vulnerabilities simultaneously, as vulnerability management consumes valuable time, resources, and the attention of security teams. Instead, they need to prioritize them and address the ones that require immediate fixes.
Vulnerability management is no longer just about finding flaws, but also about understanding which issues truly matter in the context of your business. Without prioritization, your teams will focus on low-priority, low-impact flaws while overlooking vulnerabilities that could cause severe damage. The goal is not to fix everything, but to prioritize your vulnerabilities in a way that delivers the maximum reduction in risk with the resources available.
This article highlights the limitations of the traditional vulnerability prioritization method. It lists the contextual factors that you must consider when prioritizing vulnerability. It explains how modern, AI-powered risk-based vulnerability prioritization works. It also explores the framework for implementing risk-based vulnerability prioritization.
The Problem with Traditional Scoring
Prioritizing vulnerabilities and managing them traditionally involves scoring the vulnerabilities based on the Common Vulnerability Scoring System (CVSS). This method helps measure the severity of the flaws and assigns a score to each, ranking them accordingly.
CVSS is a standardized method. It implies that while providing a baseline, CVSS does not take into account any business context; it does not reflect the reality that every organization operates in unique conditions.
CVSS might assign a “critical” rating to a vulnerability based on its technical severity, even if it only affects a non-essential system isolated from the internet. Meanwhile, it could give a “medium” rating to a vulnerability in a business-critical system, which may actually pose greater risk due to accessibility, regulatory exposure, or financial implications.
CVSS rates vulnerabilities in a static manner and does not account for asset criticality or business impact, leading security teams to make poor prioritization decisions. This is where risk-based vulnerability management comes in. It takes contextual data, such as business-criticality and likelihood of exploitation, into consideration while assigning severity ratings.
Key Contextual Factors for Vulnerability Prioritization
When transitioning from traditional vulnerability scoring, it is essential to consider the context based on the following factors and prioritize vulnerabilities accordingly.
1. Asset Criticality and Asset Context
Not all assets are created equal. For instance, an unsecured customer database in testing systems, containing synthetic data, carries no risk. In contrast, a similar vulnerability on a production server hosting sensitive customer data poses serious risks to customer privacy and your business. The latter needs to be prioritized and addressed first. So, the criticality of an asset to your business determines its priority.
By assessing asset criticality, you can focus your remediation efforts, judiciously channeling your limited capacity to identify and fix vulnerabilities that can affect your business continuity, regulatory compliance, and customer trust.
2. Exploitability & EPSS
The severity of a vulnerability is one thing, but the likelihood of someone exploiting it is more critical. For instance, a simple flaw that attackers can exploit without requiring a login is more serious than a similar vulnerability that requires administrative privileges to exploit, even if they have the same CVSS score.
The likelihood of real-world attacks for various vulnerabilities can be determined using tools like the Exploit Prediction Scoring System (EPSS). Making decisions based on EPSS data and prioritizing vulnerabilities that are more likely to be exploited helps you patch active threats promptly, rather than chasing every patch.
3. Threat Intelligence and KEV
Threat intelligence is a collection of data and insights about current cyber threats. It encompasses extensive knowledge of those threats, including the modus operandi of the attacks, the tools used, and the vulnerabilities they actively target.
Known Exploited Vulnerabilities (KEV) is a constantly updated list of vulnerabilities that are widely known to be actively exploited. KEV is maintained by cybersecurity agencies, such as the Cybersecurity and Infrastructure Security Agency (CISA), and is backed by governments.
Known Exploited Vulnerabilities (KEV) and threat intelligence integration enable you to gain actionable insights about vulnerabilities that are currently exploited by bad actors and prioritize real threats, rather than hypothetical ones.
4. Business Context and Impact
While technical severity is a significant factor in prioritizing vulnerabilities, it must always be weighed against business impact. If a vulnerability can directly impact revenue, compliance, or operational outcomes, it should be treated as a high priority and remediated first, even if CVSS places it lower in severity. These are leadership priorities, and you should align the security actions with them.
For instance, a vulnerability in a bank’s customer login page has far more direct impact on business outcomes than a similar vulnerability in the employees’ internal communication platform of the bank, as the former directly handles customer funds, and an attack could potentially lead to fraud, loss of customer trust, and regulatory penalties.
5. Effort to Fix / Remediation Constraints
One of the most critical factors that determines the priority of a vulnerability is the effort required to fix it. Sometimes, you will be right to grasp the low-hanging fruit first. Prioritizing medium-risk vulnerabilities that are easy to patch over a high-severity flaw that requires weeks of complex work gives quick wins. Balancing the cost of remediation and effectiveness ensures optimal outcomes.
An Example of Prioritizing Vulnerabilities Based on Multiple Factors
By incorporating the above-mentioned five factors, you can start prioritizing vulnerabilities based on context. For instance, this approach might assign a higher priority to a medium CVSS vulnerability on a high-value asset that is already being exploited in the wild than a critical vulnerability with no exploit history. This is the essence of risk-based vulnerability management aligned to real-world conditions rather than theoretical ratings.
Implementation Framework
You can adopt the risk-based vulnerability management approach by following a structured framework:
- Discovery and Inventory: Gain visibility of all your digital assets by doing an audit of all the assets across on-premises and cloud environments.
- Contextual Enrichment: Align vulnerability prioritization with operational and business realities by adding multiple layers of context, including asset criticality, exposure level, business importance, and existing controls.
- Scoring and Prioritization: Combine CVSS scores, EPSS data, KEV lists, threat intelligence integration, and business context into a comprehensive ranking system.
- Decision and Remediation: Assign resources to address high-priority vulnerabilities as per the list. Address easy-to-patch vulnerabilities first, especially if it significantly reduces overall risk.
- Continuous Feedback Loop: Vulnerability management is a continuous process; you need to constantly learn from security incidents and adapt your approach to new business needs. You should continually refine your vulnerability management strategy in response to evolving threat landscapes.
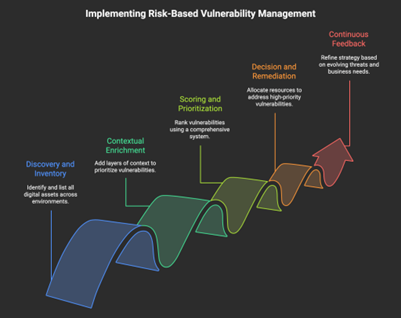
By following these steps, you can move from reactive patching toward proactive, context-driven prioritization.
Modern Methodologies: AI and 4th Generation Prioritization
While incorporating multiple factors makes the process of prioritizing and patching vulnerabilities multidimensional and more effective, manually handling all of these tasks can make vulnerability management painfully slow. This is where 4th generation vulnerability prioritization powered by artificial intelligence comes in. It takes all these factors into account and introduces automation to vulnerability prioritization, making vulnerability management easier.
Platforms capable of 4th generation vulnerability prioritization implement risk-based vulnerability management by combining threat intelligence integration, EPSS predictions, KEV data, asset value, and compensating security controls. They automate the process of pulling data from various sources and combining them to provide precise rankings and actionable insights on what to address first.
The Case for Cyber Risk Quantification (CRQ)
While you can assign priorities for various vulnerabilities effectively using AI and adopting a risk-based vulnerability prioritization approach, you still need resources to address them. To get the resources approved and sanctioned, you need to communicate the vulnerabilities to business executives and explain why you prioritize patching them in a specific order, thereby creating buy-in. But they often do not understand technical scoring. It is crucial to translate all of this into business language that executives can understand. This is where Cyber Risk Quantification (CRQ) becomes powerful.
Cyber Risk Quantification helps express risks in terms of financial exposure. For example, with Cyber Risk Qualification, you can estimate the potential financial impact of an unpatched flaw on the company to be around $2 million in terms of downtime and fines. This way, you can convince the executives and gain stronger buy-in and budget support from them. Linking vulnerabilities to measurable business impact transforms vulnerability management into a boardroom priority.
Final Thoughts
New vulnerabilities are identified every day, but you cannot fix them all at once, because your resources are finite. It is crucial to identify what matters the most at any given time and fix it first. You can achieve that by prioritizing vulnerabilities based on context. It helps you focus on real risks rather than arbitrary severity ratings.
Integrating risk-based vulnerability management and prioritizing vulnerabilities based on context empowers your security teams to align their actions with your business goals, operational impact, and real-world threats, thereby optimizing remediation efforts and reducing exposure to real-world threats.
Prioritizing based on context and patching the right things helps organizations move from reactive patching to strategic defense.
FAQs
1. What is vulnerability in the context of security?
A vulnerability is a flaw that could cause a security issue. It could be a misconfiguration, or weakness in software, hardware, or processes that attackers can exploit to compromise systems, gain unauthorized access, or disrupt operations.
2. How are vulnerabilities prioritized?
Vulnerabilities are prioritized by combining severity ratings with context such as asset criticality, exploit likelihood, threat intelligence, and business impact. This ensures organizations focus remediation efforts on the risks that truly matter.
3. What is vulnerability priority rating?
A vulnerability priority rating is a score or ranking that helps security teams determine which vulnerabilities to address first. It balances technical severity with contextual factors, such as the likelihood of exploitation and the potential business impact.
4. What is the first step in vulnerability management?
The first step in vulnerability management is gaining complete visibility into all assets. This discovery and inventory phase ensures that every system, application, and device is monitored for potential vulnerabilities.
Since you’re here… At VFM, we are committed to helping businesses secure their digital future. Explore how our tailored IT infrastructure and cybersecurity solutions can empower your enterprise to achieve more.
Our team is here to collaborate with you, whether it’s through tailored solutions, expert advice, or impactful partnerships. From strengthening your IT ecosystem to driving innovation, let’s work together to build resilient systems for tomorrow.
Here’s How You Can Engage with Us:
- Stay Connected: Follow our latest updates, insights, and events on LinkedIn.
- Collaborate with Us: Partner with us to enhance your IT infrastructure or cybersecurity systems.
Let’s work together to drive success and secure your enterprise.
Contact Us | Explore Our Services


