Vulnerability Detection and Patching
While constantly monitoring network traffic, securing privileged accounts, keeping an eye out for security breaches, containing attacks, and minimizing the blast radius are some crucial activities involved in securing your IT infrastructure, it is equally important to take preventive measures such as vulnerability detection and patching, regardless of how unglamorous these activities could be.
These tasks are foundational to enterprise cybersecurity in the age of ransomware, AI-driven threats, and zero-day exploits. Preventing these attacks is more cost-effective than countering them. So, you must fortify your cyber defenses with vulnerability detection and patching.
This article examines the importance of consistent vulnerability detection and patching for maintaining cyber hygiene, outlines the steps for effective implementation, discusses the consequences of failing to patch the vulnerabilities, presents best practices in vulnerability detection and patching, and explores the challenges and mitigation strategies associated with these processes.
What are the Common Vulnerabilities in an Enterprise IT Setup?
Some of the most common vulnerabilities include:
- Misconfigurations
- Outdated software and OS
- Missing patches
- Weak or default passwords
- Improper access controls
- Misconfigured cloud services
- Excessive privileges to user accounts
- Unsecured APIs
- SQL injection flaws
- Cross-site scripting (XSS)
- Missing input validation
- Insecure deserialization
- Exposed ports and services
- Lack of encryption for sensitive data
If these vulnerabilities are not patched on time, they can be exploited by attackers.
What is Vulnerability Management?
Vulnerability management is the practice of identifying, evaluating, prioritizing, and remediating security weaknesses in the enterprise IT setup so that they can be addressed before a bad actor can exploit them and harm your company by means of:
- Ransomware attacks
- System compromises
- Privileged access breaches
- Unauthorized access to sensitive information
- Data theft or
- Service disruption
Why is Vulnerability Management Important?
Vulnerability management is critical because the greatest risk often comes from known vulnerabilities that are yet to be patched. It is easier to fix them by continuously identifying security flaws in software and systems and remediating rather than containing a breach and managing the situation post-attack.
When known vulnerabilities are not patched in a timely manner, they leave their attack surface wide open, allowing attackers to exploit them and gain access to your critical systems. According to Tenable’s 2022 Threat Landscape Report, the most commonly exploited vulnerabilities were up to five years old, confirming attackers frequently target known and unpatched flaws. Vulnerability detection and proactive patching are therefore critical to reducing the likelihood of a breach.
What are the Steps Involved in Vulnerability Management?
Vulnerability management is a continuous process that involves:
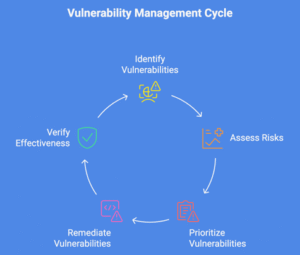
1. Identification
Vulnerability management starts with vulnerability scanning. During this process, automated scanning tools constantly look for vulnerabilities and security weaknesses across systems, applications, networks, and endpoints, covering both internal and external-facing assets.
2. Vulnerability Risk Assessment
After identifying the vulnerabilities, you must conduct a vulnerability risk assessment and determine how these vulnerabilities could potentially impact the organization.
Not all vulnerabilities are equally dangerous. Depending on the risks posed by the vulnerabilities, you must assign risk scores to each of these risks. The risk scores should be assigned based on how exposed the affected asset is, how critical the asset is in your IT setup in terms of accessibility and sensitivity of data it contains, and whether there are known exploits actively being used in the wild. Risk scoring often follows the Common Vulnerability Scoring System (CVSS) or a custom risk model.
3. Vulnerability Prioritization
Once you have assessed and ranked the vulnerabilities, it is crucial to implement vulnerability patch prioritization. You must focus on severe flaws in high-value assets, such as critical servers and systems that can seriously impact the business if breached. These vulnerabilities must be patched first.
4. Remediation
The next step involves remediating the vulnerabilities as per the priority. Timely remediation requires the participation of multiple departments. You must coordinate across IT and security teams and ensure minimal disruption to operations. Depending on the nature of the vulnerabilities and flaws, you can patch them by applying security patches and configuration changes, or implementing compensating controls, such as network segmentation or firewall rules. If you cannot completely patch a vulnerability, you can apply temporary workarounds to reduce the risk.
5. Verification
After completing these actions, it is indispensable to verify whether remediation actions prove effective, resolve the vulnerability, and have not led to any new issues. This step ensures that the systems are secured and the risks are mitigated.
Vulnerability Management Best Practices
Following are some of the best practices organizations should follow to identify and patch vulnerabilities effectively and efficiently.
- Vulnerability management is a continuous process. So, you must regularly scan all your IT assets continuously and schedule your regular patching cycles.
- To identify vulnerabilities and patch them, your teams must first know the devices and hardware currently in operation within the organization and the versions of operating systems, software, business systems, and third-party tools currently in use. So, you must maintain updated inventories of hardware, software, and endpoints.
- Prioritize detection and patching of assets based on criticality and exposure.
- Enable real-time, automated vulnerability management by integrating vulnerability detection tools with Security Information and Event Management (SIEM) and risk assessment platforms.
- Speed up remediation and reduce human errors by automating patching. Automated patching combined with vulnerability prioritization makes the vulnerability remediation process quicker and reduces the Mean Time To Remediate (MTTR).
- Test the patches before applying them by validating them in sandbox environments.
- Run post-patching scans to confirm closure of vulnerabilities.
Integrating Detection and Patching for Continuous Hygiene
When you identify multiple vulnerabilities, prioritize them, and address them one by one, there could be silos between the processes of detection and remediation. These gaps could lead to delays and miscommunication. So, it is indispensable to unify detection and patching. Integrating these processes into a unified vulnerability management system ensures:
- Automatic triaging of identified vulnerabilities and patch scheduling.
- Collaboration of security and IT teams through shared dashboards.
- Continuous tracking and optimization of vulnerability management metrics over time.
- Continuous cyber hygiene and operational efficiency.
Vulnerability Patching Challenges and Mitigation Strategies
Vulnerability detection and patching pose several challenges.
- Sometimes, you may not have the resources, time, and personnel to patch everything on time. Nevertheless, you can address the situation through vulnerability patch prioritization. You can patch vulnerabilities based on risk scores, leaving the lower-risk vulnerabilities to be patched later. At the same time, you must communicate it properly to the stakeholders and achieve alignment between security and operations.
- You may have legacy hardware, software, and systems, and fixes and patches may not be available for them. You may be forced to upgrade them, which may not be feasible due to compatibility issues, operational dependencies, or cost constraints. In those cases, it may be hard to patch them permanently or find suitable workarounds. In these cases, you must segment these legacy systems using VLANs, firewalls, or access control lists (ACLs) to minimize exposure and isolate risks.
- Sometimes, patches can break applications when applied. You can prevent this by ensuring coordinated patch scheduling and testing them in a safe, sandbox environment.
Final Words: Why This Matters More Than You Think
In cybersecurity, prevention is better than a cure. Since most breaches occur due to known yet unpatched vulnerabilities, you can prevent security incidents by identifying these vulnerabilities constantly and fixing them. What you do not fix may potentially hurt you, and unaddressed vulnerabilities can become points of entry for attackers. So, a unified vulnerability detection and patching process is inseparable and the most essential hygiene practice involved in ensuring cybersecurity.
By prioritizing vulnerability risk assessment, continuous vulnerability scanning, and automated patching, organizations can significantly reduce their exposure to attacks and build resilience into their infrastructure.
Building a truly secure enterprise requires starting with the basics. And nothing is more foundational than timely, consistent vulnerability detection and patching.
FAQs
1. What is the difference between patching and vulnerability?
A vulnerability is a security flaw in a system, while patching is the process of fixing that flaw by applying updates or code corrections to prevent exploitation.
2. What is vulnerability scanning and patching?
Vulnerability scanning identifies security weaknesses in systems, applications, and networks. Patching is the follow-up action that fixes those identified vulnerabilities to reduce the risk of cyberattacks.
3. What do you mean by vulnerability detection?
Vulnerability detection refers to the process of finding security flaws in your IT infrastructure using automated tools that scan systems, software, and configurations for known threats or weaknesses.
4. What are the 5 steps of vulnerability management?
The five key steps include identifying vulnerabilities, assessing their severity and impact, prioritizing vulnerabilities based on risk, remediating through patches or controls, and verifying the fix to ensure effectiveness.
Since you’re here… At VFM, we are committed to helping businesses secure their digital future. Explore how our tailored IT infrastructure and cybersecurity solutions can empower your enterprise to achieve more.
Our team is here to collaborate with you, whether it’s through tailored solutions, expert advice, or impactful partnerships. From strengthening your IT ecosystem to driving innovation, let’s work together to build resilient systems for tomorrow.
Here’s How You Can Engage with Us:
- Stay Connected: Follow our latest updates, insights, and events on LinkedIn.
- Collaborate with Us: Partner with us to enhance your IT infrastructure or cybersecurity systems.
Let’s work together to drive success and secure your enterprise.
Contact Us | Explore Our Services


